How to deal with online harassment and threats: Difference between revisions
No edit summary |
No edit summary |
||
| Line 58: | Line 58: | ||
<h2>More information and resources</h2> | <h2>More information and resources</h2> | ||
<h3> Resources | <h3> Resources for putting this into practice</h3> | ||
* [https://open.nytimes.com/how-to-dox-yourself-on-the-internet-d2892b4c5954 How to Dox yourself on the Internet] by the New York Times | * [https://open.nytimes.com/how-to-dox-yourself-on-the-internet-d2892b4c5954 How to Dox yourself on the Internet] by the New York Times | ||
| Line 68: | Line 68: | ||
** [https://help.instagram.com/426700567389543 Instagram’s guide to blocking] | ** [https://help.instagram.com/426700567389543 Instagram’s guide to blocking] | ||
** [https://help.snapchat.com/hc/en-us/articles/7012410297364-How-to-Remove-a-Friend-on-Snapchat Snapchat’s guide to blocking] | ** [https://help.snapchat.com/hc/en-us/articles/7012410297364-How-to-Remove-a-Friend-on-Snapchat Snapchat’s guide to blocking] | ||
<h3> | <h3>Free online learning courses</h3> | ||
<ul> | <ul> | ||
<li>[https://advocacyassembly.org/en/courses/34/#/chapter/1/lesson/1 Recognising and Responding to Online Gender-Based Violence], a free online course by Advocacy Assembly and Association for Progressive Communications (APC) | <li>[https://advocacyassembly.org/en/courses/34/#/chapter/1/lesson/1 Recognising and Responding to Online Gender-Based Violence], a free online course by Advocacy Assembly and Association for Progressive Communications (APC) | ||
<li>You will learn about different types of online gender-based violence, how it harms people, and how people are responding. You'll also learn effective strategies and digital safety steps. | <li>You will learn about different types of online gender-based violence, how it harms people, and how people are responding. You'll also learn effective strategies and digital safety steps.</li> | ||
<li>[https://advocacyassembly.org/en/courses/43 Cyber harassment: Concepts and prevention] by Advocacy Assembly and Institute for War and Peace Reporting | <li>[https://advocacyassembly.org/en/courses/43 Cyber harassment: Concepts and prevention] by Advocacy Assembly and Institute for War and Peace Reporting | ||
<li>You will also learn some general digital security concepts, about metadata, and how to do safe online campaigning.</li> | <li>You will also learn some general digital security concepts, about metadata, and how to do safe online campaigning.</li> | ||
<li>[https://advocacyassembly.org/en/courses/32 Staying Safe Online And Using Social Media] by Advocacy Assembly and Security First | <li>[https://advocacyassembly.org/en/courses/32 Staying Safe Online And Using Social Media] by Advocacy Assembly and Security First | ||
<li>By the end of the course, you will be able to identify common causes of digital security breaches such as phishing and social engineering. Also how to implement basic precautions to protect from viruses and an stay safe online in repressive countries.</li> | <li>By the end of the course, you will be able to identify common causes of digital security breaches such as phishing and social engineering. Also how to implement basic precautions to protect from viruses and an stay safe online in repressive countries.</li> | ||
<li>How to protect your identity online | <li>[https://learn.totem-project.org/courses/course-v1:Totem+TP_IO_EN+001/about How to protect your identity online] on the Totem Project | ||
[https://learn.totem-project.org/courses/course-v1:IWMF+IWMF_OH_EN+001/about Know your trolls] on the Totem Project created by IWMF | <li>By the end of this course, you will: Understand what anonymity is; Know what identifies you online; Understand why protecting your identity and that of others matters; Know what to do to protect your identity; Understand that achieving anonymity online is often very difficult. | ||
<li>After completing this interactive course you will:Recognize types of online abusers and how they work together, Become more familiar with some of the tactics online abusers use, Be equipped with some key strategies for dealing with abuse | <li>[https://learn.totem-project.org/courses/course-v1:IWMF+IWMF_OH_EN+001/about Know your trolls] on the Totem Project created by IWMF | ||
<li>After completing this interactive course you will: Recognize types of online abusers and how they work together, Become more familiar with some of the tactics online abusers use, Be equipped with some key strategies for dealing with abuse | |||
<h3>Video resources</h3> | <h3>Video resources</h3> | ||
Revision as of 16:59, 8 February 2024
The information below is used with permission from the Totem Project's online course on Know Your Trolls, in 2023.
Abusers and their tactics
Watch this video to get an understanding of the strategies used and the reason abusers use them.
Identifying common tactics
Targets need a common language to describe what’s happening to them, to friends, colleagues, editors, and law enforcement. You will learn more about how to define these tactics in the next exercise. You may find that abusers often use a combination of tactics to silence you online. Below are some common tactics and their definitions.
More on doxxing
Doxxing is a tactic used by online abusers as a way to intimidate and threaten journalists. Personal details, including a home address, are posted online with a call to others to use that information to harass and cause harm.
This is a common tactic used by the far right as well as by members of certain interest groups, such as pro-life supporters. Having your home address circulated online by trolls means that an online attack has the possibility to turn into a physical threat as people now know where you live.
There are steps you can take to remove and limit access to your personal information on the Internet. This will help to better protect you against doxxing. Learn more about this in the Totem course on How to protect your identity online.
Mental health
Online harassment and abuse can take its toll on your mental health. There are steps you can take to protect yourself and reduce the impact of the abuse.
- Ask a colleague or friend to monitor your accounts so you do not have to be exposed to the abuse
- Do not engage with trolls as this can make the situation worse.
- Speak with your editor or colleagues about the abuse and make them aware of the situation.
- Take care of yourself by looking after your body and mind.
Ways to fight back
Documenting attacks
It can be important to document the abuse you are receiving online, especially if you feel there is a threat to your life. You should keep an evidence trail to show your colleagues, editors or the authorities. This information can also be presented to international organizations who assist journalists, and they may be able to help you with your case.
- Keep a spreadsheet with details of the harassment, including date, time and type of harassment. Include the medium through which the abuse happened, for example, direct message, and also note down the platform.
- Take screenshots of the abuse. Ensure that you include, where possible, the name or handle of the abuser, the date and time, and the full content of the abuse. It’s important to capture the whole message, the date, the name, and the handle/account name when collecting evidence about your abusers. This will become important if you decide to contact the authorities or an organization that defends freedom of expression about your case.
- You may wish to ask someone to help you do this if the abuse is taking its toll on your mental health. For example, ask a colleague to monitor your social media accounts and enlist their help in taking screenshots of the abuse.
- Before you start working on a story, think about the groups of people who could attack you online as a result of publishing a story. Take steps to secure your data and your accounts: use strong and unique passwords, and protect yourself against phishing attacks.
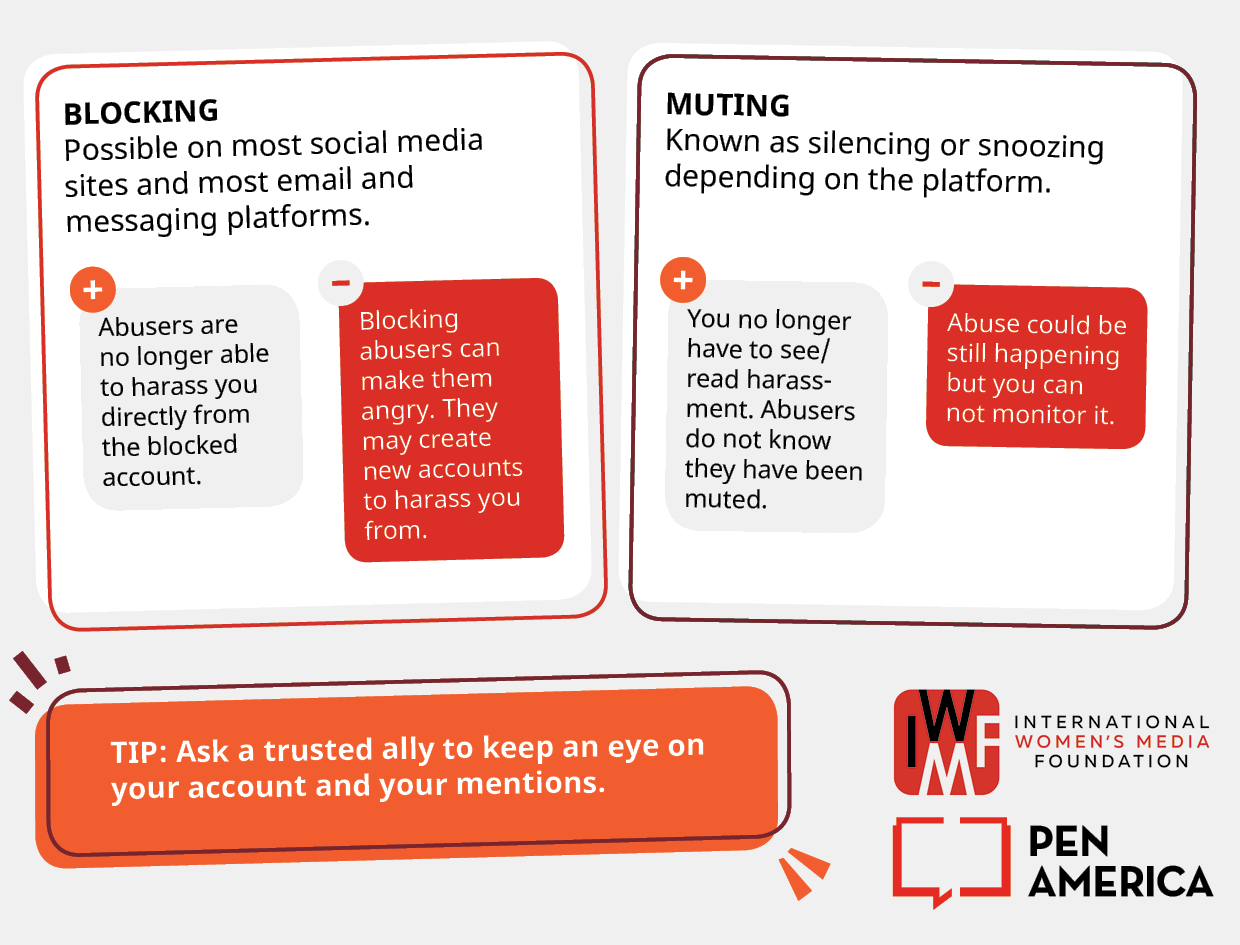
Blocking, muting, and reporting abuse
We have looked at how to document abuse. Now let’s look at how to block, mute, and report your abuse.
Tip: When you block someone on a social media site it could mean that the content they posted will be deleted. Make sure you have documented the abuse before blocking anyone.
Blocking and muting on specific platforms
Learn more about blocking and muting different social media sites by visiting their guides. Below is a list of the most common social media sites.
Platforms and reporting harassment
Each platform has different policies around reporting online harassment that makes it challenging and frustrating for those trying to get something done about their online harassment. Know that you are not alone with this. It can help to keep a record of when you reported the harassment to the platform and what, if any, were the outcomes. You can add this to other evidence that you have collected about your harassers.
Tip: Platforms administrators are only likely to take down content if it violates their community guidelines or standards. Before reporting harassment to the platform, make sure you are familiar with their guidelines and what they will and will not remove. Use the guidelines to support your case for removing the content. Below is a list of the most common social media sites:
If you are a freelance journalist or HRD working without the support of a media outlet or if you are not supported by your workplace, then you should consider reaching out to other women journalists to create a support network. You should ask them to:
- Help report abuse on the platforms
- Help document the abuse
- Monitor your social media and/or email accounts
- Make a public statement of solidarity [TIP: Focus on condemning the behavior, not the abusers]
- Rally a supportive community
- Provide emotional support
More information and resources
Resources for putting this into practice
- How to Dox yourself on the Internet by the New York Times
- Remove Personal Data from the Internet by the Committee to Protect Journalists (CPJ)
- Online Harassment Field Manual: Steps for Safeguarding Employees by PEN America
- Blocking and Muting on Different Social Media Sites:
Free online learning courses
- Recognising and Responding to Online Gender-Based Violence, a free online course by Advocacy Assembly and Association for Progressive Communications (APC)
- You will learn about different types of online gender-based violence, how it harms people, and how people are responding. You'll also learn effective strategies and digital safety steps.
- Cyber harassment: Concepts and prevention by Advocacy Assembly and Institute for War and Peace Reporting
- You will also learn some general digital security concepts, about metadata, and how to do safe online campaigning.
- Staying Safe Online And Using Social Media by Advocacy Assembly and Security First
- By the end of the course, you will be able to identify common causes of digital security breaches such as phishing and social engineering. Also how to implement basic precautions to protect from viruses and an stay safe online in repressive countries.
- How to protect your identity online on the Totem Project
- By the end of this course, you will: Understand what anonymity is; Know what identifies you online; Understand why protecting your identity and that of others matters; Know what to do to protect your identity; Understand that achieving anonymity online is often very difficult.
- Know your trolls on the Totem Project created by IWMF
- After completing this interactive course you will: Recognize types of online abusers and how they work together, Become more familiar with some of the tactics online abusers use, Be equipped with some key strategies for dealing with abuse
Video resources
- The Problem with “Don’t Feed the Trolls” by Steph Guthrie, TEDxToronto
- Stop the Trolls: Women Fight Online Harassment Panel by Feminist Frequency
- Anita Sarkeesian, Feminist Frequency at XOXO Festival
- Basic Countermeasures for Journalists to Cope with Online Harassment by IPI and the Dart Centre
- Legal Remedies to Address Online harassment by International Press Institute (IPI)
Read
- Attacks and Harassment: The impact on female journalists and their reporting [PDF] by the International Women’s Media Foundation (IWMF)
- Online Harassment Field Manual by Pen America
- Take Back the Tech website
- Social Media: Trolling and Doxxing by the Rory Peck Trust
- Dealing with Hate Campaigns: Toolkit for Journalists by the Dart Center
- A Guide to Protecting Yourself During Online Harassment Attacks by Feminist Frequency
- OnlineSOS is a non-profit organization connecting people with information and tools to take action in the face of online harassment
- Digital Security Tips and Links to Organisations who can Assist by the Global Investigative Journalism Network
- How to Manage Trolls and your Mental Health by the Dart Centre
- Tips for Allies and Witnesses by PEN America
- Totem course handouts: