February 24 2022 GM: Difference between revisions
No edit summary |
|||
| (3 intermediate revisions by the same user not shown) | |||
| Line 58: | Line 58: | ||
* Also, some more graphs from [https://metrics.torproject.org/userstats-bridge-combined.html?start=2021-11-26&end=2022-02-24&country=ru Tor metrics and the PT use in Russia]. | * Also, some more graphs from [https://metrics.torproject.org/userstats-bridge-combined.html?start=2021-11-26&end=2022-02-24&country=ru Tor metrics and the PT use in Russia]. | ||
[[File:PT1_24FEB2022.png| | [[File:PT1_24FEB2022.png|right|350px]] | ||
* Here are graphs where you can see users shifting from plain Tor to meek, obfs4, and and snowflake. | * Here are graphs where you can see users shifting from plain Tor to meek, obfs4, and and snowflake. | ||
| Line 80: | Line 80: | ||
* Growing and stabilizing the refraction networking deployment and expanding pluggable transports for clients. | * Growing and stabilizing the refraction networking deployment and expanding pluggable transports for clients. | ||
* For anyone not familiar with the term, here is some information about [https://refraction.network/refraction networking], e.g. Telex, TapDance, Conjure. | * For anyone not familiar with the term, here is some information about [https://refraction.network/refraction networking], e.g. Telex, TapDance, Conjure. | ||
[[File:PT2_24FEB2022.png| | [[File:PT2_24FEB2022.png|right|350px]] | ||
'''How the partnership with the ISP articulates:''' | '''How the partnership with the ISP articulates:''' | ||
* It involves intercepting traffic at the ISP or network operator level, and redirecting traffic from perceived “safe” addresses to user-requested, blocked content. | * It involves intercepting traffic at the ISP or network operator level, and redirecting traffic from perceived “safe” addresses to user-requested, blocked content. | ||
Latest revision as of 15:16, 24 February 2022
| Glitter Meetups |
Glitter Meetup is the weekly town hall of the Internet Freedom community at the IFF Square on the IFF Mattermost, at 9am EST / 1pm UTC. Do you need an invite? Learn how to get one here.
Pluggable Transports Meetings
Pluggable Transports (PT) are being developed and used to circumvent Internet censorship. If you use any VPNs, the Tor network or other services to access blocked content in you network, chances are that you are using PTs in the background. This monthly meetup welcomes users, developers and PT enthusiasts to share their news/updates happening once per month.
Date: Thursday, February 24th
Time: 9am EST / 2pm UTC
Who: Facilitated by Vasilis, this is their project https://magma.lavafeld.org/
Where: As a guest of the Glitter Meetup on IFF Mattermost Square Channel.
- Don't have an account to the IFF Mattermost? you can request one following the directions here.
Please note: The upcoming meeting could be in a different platform, maybe BigBlueButton or in the Mattermost but at a different time? We'll see after the first event
Notes: Please put notes here: https://pad.riseup.net/p/plugasadcaawer-keep
Notes
Community Updates
- Tor roadmapping PT support in their Rust-based Tor client
- Lessons from the Jan shutdown in Kazakhstan for circumvention (certain reachable ports and DNS tunneling).
- It's great to see that anti-censorship works even in very tough situations where large portions of the networks are blocked! Kudos and bravo to all the community for helping circumvent censorship in Kazakhstan.
- Load-balancing the Snowflake bridge to cope with an increase in users.
- New videos from the PT Implementers' Meeting of last fall.
Pluggabble Transports Meeting
This time our guest is Vasilis (@anadahz on Mattermost), an awesome person who has been guiding us through the pluggable transport world. Pluggable Transports (PT) are being developed and used to circumvent Internet censorship. If you use any VPNs, the Tor network or other services to access blocked content in you network, chances are that you are using PTs in the background
For those who are not familiar with pluggable transports the software site might look a bit scary at first sight, i guess it’s useful to visit first the main site of the project Pluggable Transports.
Tell us everything about this site: Software Pluggable Transports
- Many people from the community mentioned that it's hard to find a place that has a list of software (libraries, clients/servers, implementation) related to PTs.
- We created this website with the hope that people will be adding/editing/updating entries there.
- Hopefully it will be used as the one-stop to the PT software.
- Once could add a PT software by opening a pull request on Github or by just adding a comment on the issues. There are detailed instructions here
- Also if people do not like Github, feel free to contact/msg me and I can add software to the website
So how would you describe the audiences to which this website is targeted?
- Mainly curious people on PT software and developers.
What is the state of pluggable transport use from Russia?
- We don't have timestamps, but this recent interview touches on how users adapted to using pluggable transports after vanilla tor was blocked in Russia recently.
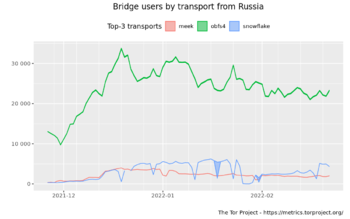
- Also, some more graphs from Tor metrics and the PT use in Russia.
- Here are graphs where you can see users shifting from plain Tor to meek, obfs4, and and snowflake.
- The snowflake numbers since Jan 25 are wrong -- they are actually about 4× what is shown. This is a side effect of the load balancing at the bridge.
On another note: in preparation for upcoming network disruptions. How hard/easy will it be to deploy dnstt on Android or iOS?
- dnstt is a PT that routes traffic via DNS responses. It is usually a slow PT but in most of the cases DNS traffic is not blocked during large Internet disruptions.
- There are some third-party apps that embed the dnstt code and run their own servers.
People here mentioned that you uploaded the videos from last PTs conference? Could you share the link? Maybe some tip of a must-watch video?
- Here is the main page with all the public videos from all days: here
- Also, the PTIM recap posts can be found here:
Refraction Networking
Growing and stabilizing the refraction networking deployment
- Growing and stabilizing the refraction networking deployment and expanding pluggable transports for clients.
- For anyone not familiar with the term, here is some information about networking, e.g. Telex, TapDance, Conjure.
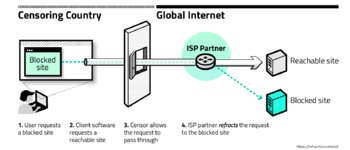
How the partnership with the ISP articulates:
- It involves intercepting traffic at the ISP or network operator level, and redirecting traffic from perceived “safe” addresses to user-requested, blocked content.
- Such an approach increases the cost of censorship, by preventing censors from selectively blocking only specific servers/websites.
- The refraction networking developers have to reach an agreement with an ISP. They work with us to deploy this circumvention technique
Any ISPs that people would like to do this that are not yet on board?
- They wrote a paper about this topic here: Running Refraction Networking for Real
- The system is currently composed primarily of research ISPs and university networks in the US, but we are always looking for more partners -- ISPs and hopefully at some point IXPs
- Here is a summary of a research paper that reflects on one year of running refraction networking at an ISP. It touches on what is required to gain the trust and cooperation of an ISP, particularly Section 5.3.
- It will be really neat to have a list of requirements needed for an ISP to run Refraction.