The Holistic Security Protocol for Human Rights Defenders
The Holistic Security Protocol for Human Rights Defenders (the Defender’s Protocol) helps us advance our physical safety, digital security, and well-being and resilience. By following the Protocol, we enhance our individual and collective security, and can reduce the burden of attacks, harassment, and censorship on us and our communities.
The Defender's Protocol (available in over 25 languages) was created by Open Briefing and is licensed under Creative Commons BY-NC 4.0 license.
Safety and security

Seek to better understand and manage the risks that you face

Consider who your allies and adversaries are.
Understand the resources and networks that your allies might leverage in your defense. Understand the capabilities and intentions of your adversaries so that you can better judge the threat that they pose.
It can be useful to identify the individuals, organizations and institutions that are your allies and adversaries. Allies are people that you trust and who stand with you or your cause. They may have networks and other resources, including funding, that can be used to improve your safety and security or be leveraged in your defense should you experience attacks, harassment or censorship. Understanding what these resources are and appealing to each ally’s individual motivations and priorities will help you engage more effectively with them.
In contrast, adversaries may try to undermine or attack you or your organization. They are likely threatened by your activities and stand to lose something if your work is successful. They may be criminal gangs, armed groups, powerful business interests, or government officials and politicians. You can better understand the threat that these adversaries pose by considering what their likely intentions are and the capabilities that they have. For example, a troll on social media may intend to shut you down but have limited ability to actually do so; whereas local security forces may both wish you harm and have the means and impunity needed to realize that intent.
Resources:
- Exercise: Identifying Allies and Opponents (by New Tactics in Human Rights)
- Overall Framework for Context Analysis, from the Holistic Security Manual for Human Rights Defenders
Consider your vulnerabilities.
Consider how your work, identity, tactics, and other factors and characteristics increase or decrease your vulnerability or exposure to the threats.
In risk terms, ‘vulnerability’ is your exposure to a threat; it has nothing to do with weakness. There may be a threat, but if you are not exposed – or vulnerable – to it, then it does not translate into a risk for you personally. Risk exists where the threats and your vulnerabilities overlap. While most threats are external, factors that increase your vulnerability are generally internal. Some of these will be related to your work: the issues that you campaign on or the tactics that you use, for example. You will generally have a degree of control and choice over these factors. Other factors may be related to your personal identity, and include your sexual orientation, gender identity, age, ethnicity or nationality, for example. While you cannot control these characteristics, it is still important to understand how they may increase or decrease your vulnerability to the threats against you.
Resources:
- Exercise: Increased exposure exercise (by OpenBriefing)
Assess the likelihood and impact of each threat.
Assess the likelihood of an attack or other incident occurring and the impact should it occur, in order to understand the level of risk to you.
Not all the threats that you are exposed to will carry the same level of risk. You can explore this by following a systematic process to assess the likelihood of each threat occurring and the impact should it do so. This will help you better understand which risks you should focus on reducing. This is even more important if you are working with limited resources or few allies.
Start by listing all the specific threats that could potentially harm you and describe how you are exposed to each of them. Adversaries will pose a direct (targeted) threat against you. Other threats that could cause you harm or injury will be indirect. It is important to consider safety, medical and health issues as well as security concerns. You should also consider threats to your digital security and wellbeing alongside physical threats.
Considering your vulnerabilities, give each threat a score from 1-5 (very unlikely to very likely) for how likely it is to occur and a score from 1-5 (negligible to critical) for what the impact on you or your work would be. Multiplying your likelihood and impact scores together for each threat will give you a risk rating from 1 to 25. Those risks rated 1-3 can be considered very low; risks rated 4-6 can be considered low; those rated 8-10 are moderate; risks rated 12-16 are high; and those rated 20 or 25 are very high. This is known as the inherent (or unmitigated) risk.
You should conduct this exercise periodically, in response to new or changing threats or vulnerabilities or following any significant changes in the political, economic, social, or legal environment.
Resources:
- Exercise: Risk assessment matrix (by OpenBriefing)
- Identifying and Analysing Threats, from the Holistic Security Manual for Human Rights Defenders
- Risk Assessment in Human Rights Defense Methodological Guide from the Psychosocial Approach (2022) by Aluna (also available in ES)
- How to mitigate your risk of being subject to Pegasus surveillance - this page includes research on the use of Pegasus against HRDs, and a list of countries known to have purchased Pegasus
- Tips for researching threats safely
Take concrete steps to reduce the likelihood and/or impact of each of your risks.
Once you better understand the risks that you face, you can begin to think about some targeted measures to reduce those risks. You can do this by systematically reducing the likelihood and/or impact of each threat in turn. You should focus on addressing your vulnerabilities, as some of these will be under your control. It can sometimes be difficult to affect the likelihood of a threat occurring, but you may still be able to limit its impact. Be mindful that making simple changes to your behaviour and working practices will likely be cheaper and more effective than reaching for technical solutions. Combing these measures in a single list will give you a simple risk reduction plan, which you should review regularly.
If you are facing a large number of threats, it may be helpful to decide which ones to focus on first. There are a number of ways you can do this. You can choose to accept a risk, avoid it altogether, transfer or share it with others, or manage it. You might decide that you are willing to accept for now any risks that are moderate or lower, but avoid, transfer or manage all risks that are high or very high, for example. (The point above which you are not prepared to accept risk is known as your risk threshold.) This would allow you to focus your efforts and limited resources on mitigating just the high and very-high risks that you cannot avoid or transfer.
You can also reassess the threats with new likelihood and impact scores in light of the mitigation measures that you are implementing. The revised ratings will represent the residual (or remaining) risk to you. Be mindful that some of these may still sit above your risk threshold and will require further attention to lower the risk to an acceptable level.
Resources:
- Exercise: Risk reduction plan template (by OpenBriefing)
- Responding to Threats, from the Holistic Security Manual - Once we have established the threats we face and analysed them in detail, we can begin to analyse how we might respond to them.
Maintain awareness of your environment.
Maintain awareness of what is going on around you and be alert to any changes to the people and things in your environments.
Our minds instinctively seek to quickly normalise changes in the world around us. This can be very positive from a wellbeing perspective. But, from a security perspective, it means that we can miss, or even dismiss, changes that may indicate an increased risk to us or our work.
To counter this, be mindful of the people and things around you and look out for what is known in military circles as the ‘absence of the normal, presence of the abnormal’. You are seeking to maintain a state of relaxed alertness. Be mindful of individuals appearing in or disappearing from your daily routine or changes in the behaviour of those around you. This can include changes in the tone or frequency of harassment or an escalation in the attacks against you and co-workers. Likewise, be aware of new objects in your surroundings, such as vehicles or devices, or items in unusual or unexpected places. Maintaining this situational awareness may help you anticipate actions against you and give you time to react appropriately.
If you think changes in your surroundings or in the behaviour of your adversaries may indicate a new threat or an increased risk, you should take preventative actions. These could include, for example, discussing the changes with friends, family and co-workers to try and better understand the situation; changing your travel plans or moving to a safer location; or alerting your support networks that you feel at greater risk and asking them to help you.
--> Exercise: Pestle analysis exercise and template (from the Holistic Security Manual)
Identify your safety contact
Ask a trusted and capable friend, co-worker or family member to be your safety contact. At times of heightened risk, tell them in advance where you are going, what you are doing, and when you will return. Check in with your safety contact at pre-agreed regular times throughout the day. Agree with them what they will do and who they will contact should they not hear from you.
Agreeing set times when you will contact a nominated safety contact each day reduces the time between anything happening to you and your support network realising and raising the alarm or mobilising support.
In very high-risk locations or at times of significant risk, these ‘check ins’ could be as frequent as every 30 minutes. In lower-risk locations or times of reduced risk, check ins might be just once a day, in the evening. You and your safety contact need to agree what is realistic and appropriate. It is important that the check-in schedule is pegged to regular times during the day rather than when you are due to arrive or depart certain locations. This avoids any delays in your journeys resulting in missed check ins and unnecessarily worrying your safety contact.
It is essential that you and your safety contact agree the actions that they will take if you do miss a check in. It is sensible to have a phased set of responses that increase in magnitude and severity based on the number of hours since a missed check in. It is helpful for your safety contact to have access to your schedule, so that they can establish your last known location if possible. If your safety contact is an international partner, be mindful of time zone differences and the possibility of any connectivity issues causing a false alarm. International safety contacts should also be able to mobilise your local support network to try and locate you.
--> Resources: Check-in plan template (by OpenBriefing),
--> Exercise: Who is in your PACT? part of the Panic Button Training Kit (by The Engine Room)
At high-risk times or locations, travel with someone.
At high-risk times or locations, travel with friends, family members or co-workers or request international protective accompaniment.
Adversaries may be more likely to attack or harass you if they think you are vulnerable or an easy target. One practical way that your local allies can support you is by staying with you during times of heightened risk or traveling with you in high-risk locations. As an adversary’s actions may be blocked by others around you, or at least will not go unnoticed, it might raise the stakes for them enough to deter them in the short term.
Be mindful that co-workers and others staying or traveling with you may be placing themselves at risk. If you face consistent and considerable threats, you may want to instead consider requesting international protective accompaniment from a specialist organization, such as Peace Brigades International. Protective accompaniment is a non-violent but overt strategy for protecting human rights defenders and threatened communities. The volunteer accompaniers personify the international concern for human rights. Adversaries know that any attacks against defenders accompanied by international volunteers will not only be witnessed but will likely result in legal, political, diplomatic or economic repercussions.
Prepare your family and co-workers so that they are better able to cope should the worst happen:
Make a will and ensure that your family knows where your important financial and legal documents are stored.
If you are detained, kidnapped or harmed, your family or nominated others may need access to your financial and legal documents or to know your wishes in these and other important areas. You should therefore write or update a will or testament and store it together with other relevant documents in a safe place that trusted others can access under agreed circumstances. Consider the relative importance of security, ease of access, and the possibility of accidental or malicious deletion or destruction when deciding whether your safe place should be a physical location, such as a lockable drawer or safe, or an encrypted digital file.
--> Resource: Coping with prison (find this)
Develop a continuity plan with co-workers so that they can continue working in your absence.
If you are unable to work for any reason, it may be difficult for your co-workers and partners to continue activities and operations in your absence. To address this, you should together create a plan that sets out your main responsibilities and identifies who would take over each and the information and resources that they would need in order to do so. You should then share this plan with co-workers and other relevant stakeholders to reduce the possibility of conflict or confusion among them.
--> Resource: Delegated responsibility plan template (by OpenBriefing)
Help your family and co-workers draw up plans for them to relocate, seek sanctuary or asylum, or otherwise keep themselves safe from any further reprisals.
If you are detained or worse, adversaries may threaten your family and co-workers in your absence. It is important that your security and contingency planning takes this into account. Those close to you may need to go into hiding, seek sanctuary in an embassy or elsewhere, move to another part of the country, or leave the country altogether. It is essential that they make realistic plans for each of these options in advance so that they can take the most-appropriate actions at short notice to ensure their own safety.
--> Resource: Individual contingency plan template (by OpenBriefing)
Complete training in holistic security and first aid
If possible, complete holistic security training designed for human rights defenders. Also consider completing advanced first aid training and purchase individual trauma kits for your home, vehicle, and office.
The security training that is appropriate for human rights defenders is very different to the hostile environmental awareness training that is standard in the humanitarian or corporate sectors. Security training of that nature is usually designed for the international staff of organisations with significant resources who may face indirect threats from violent criminals or armed groups. In contrast, human rights defenders and those defending land, environmental and indigenous rights are more likely to be local community members with limited resources and face direct threats from highly-capable adversaries, often with state or corporate backing.
Security training for human rights defenders should focus on building an understanding of personal risk and be mindful of gender and other personal identity factors. Trainers should seek to co-develop the security strategies and tactics with participants and include many of the measures put forward in the guidance here on situational awareness, check-in schedules, accompaniment, and contingency planning, for example. It is important that the training is holistic, and goes beyond physical safety and security and includes digital security and wellbeing and resilience issues.
You may also want to consider advanced first aid training if you face a consistent and considerable threat of physical harm or live and work in areas with limited medical facilities. Appropriate training should include the essential first aid skills, such as basic life support, but focus on more-advanced skills, such as treating catastrophic bleeding and safely moving casualties. It should cover the contents of trauma kits and how to use them correctly. Crucially, it should also include how to treat yourself and how to improvise basic equipment. You should choose a course that is run over several days, and includes scenarios and practical exercises. Once you have completed the training, you should purchase individual trauma kits for your home, vehicle and office if possible.
With both security and first aid training, it is important to complete a refresher course every year and a full course at least once every three years in order to maintain and improve your skills.
Know your risk tolerance and when to ask for help
Understand the level of risk to you and your family that you are prepared to accept. Do not be afraid to ask for help or pause your work if the situation becomes riskier than you are comfortable with.
Each of us has a different level of risk that we are prepared to accept in order to achieve our goals. In risk management, this is referred to as our ‘risk appetite’. Those who defend and promote human and environmental rights often have higher risk appetites than others. But even within the same organisation – or family – there will be different personal risk appetites. For each of us, though, there is a point beyond which the risk – to ourselves or others – simply becomes too great to accept.
When considering your own risk appetite, it is important to consider the impact on your friends, family, and co-workers should you be detained or worse. It may be entirely valid for you to accept extremely high personal risk to further your cause, but it is usually only responsible to do so if you, or your support network, have the capacity to respond effectively should an incident occur.
It is important to understand that your own risk appetite will likely change over time. This may be following a major life event, such as the birth of a child, getting married or the death of a family member. Or it may follow an incident or near miss that affects you or a co-worker. Whatever the reason, it is important to recognise, understand and communicate to others any changes in your risk appetite.
--> Exercise: Risk appetite exercise (by OpenBriefing)
Digital security
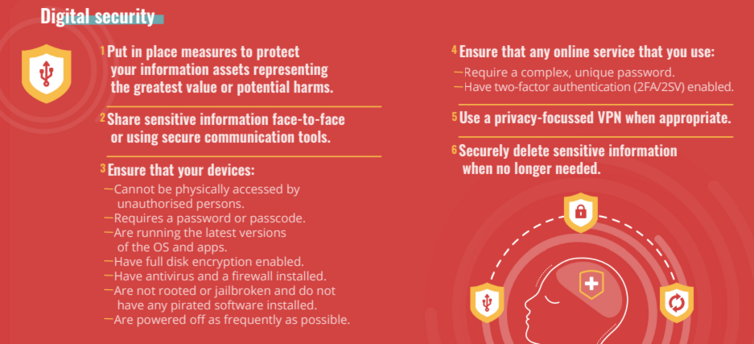
Understand and protect your information
Consider the different types of information that you hold and seek to better understand both their value to your work and the harms to you and others that could result from an attacker accessing them. Put in place additional measures to protect those assets representing the greatest value or potential harms.
The reality is that it will not be possible to protect all your information from every possible way it could be compromised, and so you must prioritize. You should proceed systematically on the basis of risk. You should consider both the value of information to your work and the potential harms to you and others that could arise if it is compromised or lost. You can also consider how likely it is that the value will be realized or that a given harm will occur. This provides a rational basis for prioritizing where you should focus your attention.
In general, you might want to:
- archive information that is both low value and low harm,
- delete information that is low value but high harm, and
- back up information that is high value and low harm.
You can then focus in the first instance on rolling out security measures for information that represents both high value and high harm.
Resources:
- Holistic Security Manual for Defenders: Understanding and Cataloguing your Information [Guide by Tactical Tech Collective and Front Line Defenders]
- Keeping Your Data Safe [Guide by EFF]
- Resources for protecting your human rights information [wiki]
Protect your communications
If it has to be shared, communicate sensitive information with co-workers face-to-face or using communication tools that allow end-to-end encryption and disappearing messages.
When you share information with others it gives your adversaries a greater chance of gaining access to it – either at the point of being sent, during the transfer itself or once the recipient has it. You can reduce the chances of a successful interception during the transfer by communicating sensitive information face-to-face – being mindful of your environment – or, if that’s not feasible, through tools that use end-to-end encryption (E2EE), such as Signal and ProtonMail. (Learn more about how encryption can help you avoid online surveillance by watching this animated overview by Electronic Frontier Foundation.)
When you use end-to-end encryption to send a message or email, it is signed (using your private key) and converted into a coded form (using the recipient’s public key) on your device before being transmitted via your and the recipient’s providers and on to the recipient’s device, where the signature is checked (using your public key) and the message or email is decrypted into readable text (using their private key). Neither the providers nor anyone who attempts to intercept the text during the transfer will be able to read the message without impractical effort.
There are still risks with end-to-end encryption. Your identity and that of the recipient – and the link between the two of you – will not be obscured, as the system needs to route the message or email between you correctly. The subject line of an email will also not be encrypted. Also, while the message or email may be secure during transfer, is still vulnerable on your device or that of the recipient if either has been compromised or is seized (disappearing messages may reduce this risk but copies could still exist). Furthermore, using end-to-end encryption may in itself raise suspicions with the authorities, particularly if there is a ban on using such technology in your country.
Remember, just as in face-to-face communication with someone you have not met before, it is vital that you verify that the person on the other end of the communication is most likely who you think they are and not an adversary. Different tools provide different ways of doing this; Signal, for example, allows you to verify unique safety numbers with each other face-to-face or through a different communications channel to help ensure that no man-in-the-middle attack is taking place.
Resources:
- Communicating with others from the Surveillance Self-Defense Guide by Electronic Frontier Foundation
- A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work?by EFF
Protect your devices
Ensure that any computer or mobile device that you use:
Cannot be physically accessed by unauthorized persons.
One of the easiest ways an adversary can gain access to your information is to gain physical access to your devices. They can then create an exact copy of your drive, for example, or install a physical monitoring device, such as a key logger.
When it comes to preventing such access, there are no hard and fast rules. For example, bringing all your devices to a protest may be impractical and increases the risk that they will be seized by police. But leaving them at home gives an adversary the opportunity to gain access to them without your knowledge. You should consider your circumstances and the likely intentions and capabilities of your adversaries and make the best judgment that you can in each situation.
Requires a password or passcode to unlock.
It is essential to protect the accounts on your devices with passwords or passcodes that are complex enough to prevent an adversary from guessing them within a reasonable timeframe. You might also consider implementing an auto-wipe feature, where the device will delete the encryption keys for all its data if a password or passcode is entered incorrectly a certain number of times. But be mindful of the risk of accidently triggering this and losing your data.
Modern devices also typically allow some biometric input to unlock a device, such as fingerprint or facial recognition. While this may be useful, be mindful that you could easily be coerced into unlocking your device in this way without having to hand over your password or passcode. Device manufacturers have recognised this concern and implemented some simple ways to quickly disable biometric access if you need to.
You should be mindful that enabling a password or passcode may only prevent an adversary logging into your user account – it may not protect the actual data. An attacker could still take a copy of the storage medium and bypass the need for a password altogether. In order to address this, you should therefore ensure that full disk encryption is enabled. This is essential for laptops and desktops that may not implement full disk encryption by default.
Is running the latest available versions of the operating system and all installed apps/software.
Almost every piece of software running on a device provides a potential avenue for an attack. Accordingly, you should limit the software installed on your device to only that which you actually need. You should also frequently – and automatically – check for updates to your operating system and any installed software and apply them as soon as possible, as they may contain important security patches.
Note that attackers can attempt to exploit this advice with fake alerts to install updates (through an unofficial channel) that will instead install malware on your device. You should treat any alert as an indication that you should perform an update in the normal way for your operating system, and, if an update is not in fact available, then you may have been the target of an attempted hack.
Has full disk encryption enabled, if legal in your country.
Full disk encryption (FDE) encrypts almost the entire hard drive of a device (or external storage media, such as USB flash drives), including the operating system and your data. This means that if your device is lost, stolen or seized, an adversary will not be able to gain access to your data by merely taking a copy of the storage. It is vital that you use a strong, unique password when enabling full disk encryption (and not the same password that you use to login to your device). However, be mindful that if you forget this password, you may lose access to your data. Also note that a strong FDE password will be undermined by a weak user account login password if this can also unlock the FDE key. The precise relationship between user account password and FDE decryption keys will depend on your device and operating system.
Resources:
Has antivirus software and a firewall installed, updated and configured correctly.
A virus is a type of malicious code or program that alters the way a computer operates. Antivirus software will traditionally scan for patterns that are indicative of known viruses and other malware. In order for this to work effectively, the antivirus must be updated with the patterns it needs to look for and the malware in question must be written to the storage device. While improvements have been made to complement this signature-based approach with heuristic checking, which checks programs for suspicious behavior that may indicate a new, unknown virus, this is not robust enough.
A firewall is used to manage the connections and flow of data inbound to your device and outbound to other devices. A firewall can detect a malicious inbound connection attempt and block it. However, it is less desirable to automatically block outbound connection attempts, as they are usually initiated by the user or legitimate programs. Attackers can exploit this by sending you a virus and tricking you into activating it. Once activated, the malware will trigger an outbound connection to a server to receive commands, additional malicious code, and to transfer your data.
Like every security measure, these limitations mean that both up-to-date antivirus and a properly-configured firewall are necessary, but not sufficient on their own.
Is not rooted or jailbroken and does not have any pirated software installed on it.
Many mobile devices have security restrictions in place; however, these are not always wanted or appreciated by users. You may be tempted to circumvent them through rooting (Android) or jailbreaking (iOS), for example, which elevate the user’s privileges on the device to the maximum available (rooting) or removes some of the restrictions on the commands that they can run (jailbreaking). This puts the device in a state that the designers had not considered, which may result in the device becoming less stable, security measures being undermined, and leaving it vulnerable to malware.
Is shut down and powered off as frequently as possible, rather than just put into sleep or hibernate state.
There are two key elements that dictate what an attacker can do in relation to your information: the attack surface (space) and the attack window (time).
The attack surface is comprised of all the devices, external storage media and written or printed materials where your information is located. It also includes you and other people who know the information. The more copies of the information that exist, the greater the attack surface and the more opportunities there are for an attacker to be successful. To limit this, you can restrict where your information is located and what forms it takes.
The attack window refers to the time when each component of the attack surface is vulnerable. The information contained in handwritten notes that are destroyed after a day are only vulnerable for that day (provided that you do not retain the information in your head). The same is true for your devices; a remote attacker will only have an opportunity to attack a device when it is switched on and running. By fully turning off your devices when they are not in use, the attack window is reduced.
There is an additional security benefit gained from turning off your devices. A virus can only perform actions for as long as the software it has exploited is running. To get around this, attackers will try to gain persistence on the compromised device so that the virus is active whenever the device is running. By turning off your devices, it means that only more sophisticated malware that can attain persistence may be effective against you over the long term. You should also consider wiping your devices and reinstalling everything as often as you can in order to remove most – but not all – persistent malware. Frequent wiping will also encourage you to limit the software installed on your device to only that which you actually need.
Resources:
- How to mitigate your risk of being subject to Pegasus surveillance, and other spyware.
Protect your accounts
Ensure that any online service that you use:
Requires a complex, unique password to access.
Online services, such as cloud storage, can ensure that your data is always available when you need it. However, they potentially increase both the attack surface and attack window by replicating your data in multiple locations and being always on.
Like with your devices, it is therefore important to use a strong, unique password for every online service. Each password must be unique – otherwise a password for one account that is compromised can be exploited by an attacker to gain access to all other services that you have used the same password for. Even any pattern that you use to generate passwords can be useful to an attacker. (You can check if you have an account that has been compromised in a data breach at Have I Been Pwned?.)
Creating and remembering numerous strong, unique passwords using traditional advice would be impossible with the number of online services you likely use. Instead, you can use an encrypted password manager to both generate suitable passwords and store your login credentials. Be mindful that an attacker gaining access to your password manager data may gain access to all your online accounts. You must therefore ensure that the password that you use to login to your password manager is itself strong, unique and memorable and that you enable two-factor authentication. As you cannot use the password manager itself to store this password, you can use one of two similar methods to manually create a strong but memorable password. You can also use these methods to create the passwords for your device user accounts and full-disk encryption:
- The passphrase method: Choose a set of four to six unrelated words that you can create a mental image from. Then substitute numbers or symbols for some of the letters in these words (though avoid common substitutions, known as ‘leetspeak’, such as 4 for A and 3 for E).
- The sentence method: Choose a long sentence that you can create a mental image from. Construct the password from the first letter of each word and then substitute numbers or symbols for some of these letters as above (again, avoiding common substitutions).
Be mindful that if you have enabled biometric access to your password manager using your fingerprint or face, this may also permit an attacker to gain access without the password.
Resources:
- Creating Strong Passwords [Guide by EFF] - This guide is designed for human rights defenders and is available in English, Spanish, French, Arabic, Russian, and other languages.
- Secure passwords [Free online course by Totem] - This course is available in: English, Spanish, French, Arabic, Russian, Farsi
- Using Password Managers to Stay Safe Online [Animated video by EFF] - Available in many languages
- Bitwarden is a free and open-source password management service that stores sensitive information such as website credentials in an encrypted vault.
Has two-factor authentication (2FA/2SV) enabled, if available.
Two-factor authentication (2FA) is an additional security measure that requires two separate, distinct forms of authentication in order to access something. For online services that support 2FA, the first factor is something you know (your password) with either something you have (a numerical code from an authenticator app) or something you are (biometrics using your fingerprint, face or voiceprint). It adds a layer of security to your online accounts, as an attacker should not be able to gain access with just your password.
Strictly speaking, when you are sent the numerical code in a text message (rather than using an authenticator app), this is two-step verification (2SV), as it is something you are sent not something you have. It is vulnerable to interception, and you should always choose to use an authenticator app, such as Authy, rather than SMS if given the option. But two-step verification is still more secure than password protection alone.
Resources:
- What is two factor authentication? [Video]
- How to enable 2fa [Guide by EFF] - Available in English, Spanish, French, Arabic, Russian and other languages.
Use a privacy-focused VPN if accessing the internet through a public or untrusted network.
When you access the internet, your internet service provider (ISP) can log the websites that you visit and may share information with the authorities. You can use software, called a VPN or virtual private network, such as Mullvad, to send your internet traffic through an encrypted tunnel from your device to one of the VPN provider’s servers and then onwards to the websites that you are visiting. This will obscure your IP address from those websites, your ISP and some network-based surveillance (though you may still be tracked in other ways, such as device fingerprinting and website trackers).
VPNs may be useful when you are accessing the internet over a public or untrusted network, such as in a cafe or hotel. If the network provider is malicious, they may be able to monitor your online traffic and even gain the passwords for your online accounts. Since the VPN provides a secure tunnel from your device to one of the VPN provider’s servers, the network operator should not be able to monitor your other online activities.
Be mindful that the VPN provider or any third-party data centres (and their ISPs) that they use might maintain traffic logs and other data that could be used to identify and/or track you. The VPN server may also be located in a jurisdiction that has a mass surveillance or bulk collection regime in place that could also unmask you and your activities through data analysis. You should also be mindful that using a VPN could in itself trigger an alert or suspicion about you and that VPNs are illegal or government controlled in several countries.
Resources:
- Safe internet browsing using VPN and Tor browser [Collection of resources]
Securely delete sensitive information in all its forms and variations as soon as it is no longer needed, and ensure that it is not recoverable.
When you delete information from your devices or external storage media, the effectiveness of this may vary. A hard disk drive (HDD) can be mostly erased by repeatedly writing random data to the entire storage area; however, this is not possible on modern solid-state drives (SSDs). On an SSD, a significant amount of data is held in an area that is kept spare to limit the wear and tear on the drive. This means that secure deletion of storage media containing unencrypted data may not be possible with software alone; proper physical destruction of the drive may be the only secure option. If you are using full disk encryption on a device – including those with SSDs – then the need for secure deletion is reduced but still present.
Be mindful that not all your information will be stored on electronic devices. You should securely store any physical media containing sensitive information, such as notebooks or print outs. When the information is no longer needed or if its continued existence presents too great a risk, you should destroy it by shredding with a cross-cut shredder and incinerating it, though the most-effective method will vary from medium to medium. The destruction must result in waste from which the original material cannot practically be recreated. Never put sensitive information in the rubbish or trash, as it is very common for the authorities to search the refuse of houses and offices to uncover documents and other compromising information.
Resources:
- How to: Delete Your Data Securely on Windows by EFF
- How to: Delete Your Data Securely on macOS by EFF
- How to: Delete your Data Securely on Linux by EFF
Well-being and resilience

Maintain good sleep hygiene, including establishing a regular nightly routine and a pleasant sleep environment, if possible.
Sleep is vital to health and wellbeing. The average adult needs seven to nine hours of sleep a night. Not getting enough quality sleep will affect so many aspects of your waking life. Sleep deprivation or disrupted sleep will affect your mood, concentration, and memory, and longer-term may weaken your immune system and raise your blood pressure, for example. Whether you tend to sleep well or have difficulties getting a good night’s sleep, it is important to maintain good habits around sleep.
As best you can, try to create a cool, dark and quiet environment in which to sleep. Remove anything to do with work from where you sleep, including your phone if possible. For at least one hour before you would like to be asleep, avoid eating, drinking (especially alcohol and caffeine), smoking, looking at screens, and all stimulating activity, including exercise. Try to put your worries and your to-do list to one side and consciously foster a state of rest and relaxation. When possible, go to bed at the same time every night and wake up at the same time each morning, going outside into natural light as soon as is practical. Regular daytime exercise will also promote the length and quality of your sleep.
Be mindful of any sudden, unexplained changes in the quality and quantity of your sleep or your usual sleep/wake schedule. Completing a sleep diary or using a tracking app, such as Sleep Cycle or SleepScore, may help you identify any changes. Changes to your sleep pattern may indicate that your sleep hygiene needs attention using the above guidelines. If your sleep does not improve, you should consult a healthcare provider or mental health professional. Sleep disorders, such as insomnia, sleep apnoea and Restless Leg Syndrome, may benefit from specialist support, such as Cognitive Behavioural Therapy (CBT) or medication.
Eat regular meals and maintain a healthy diet.
The food we choose to eat, when we eat it, and the amount we consume are all critical to our health and wellbeing. Our energy levels, mood, performance and longer-term health are all impacted by our daily choices around food.
The work we do can be demanding, and it is sometimes tempting to rely on caffeine or sugary snacks to get us through a stressful day. Likewise, busy schedules may encourage us to skip the occasional meal or eat at irregular times, such as late at night. These choices will contribute to spikes and crashes in your blood sugar levels, and may leave you craving more carbohydrates than you actually need. Longer-term, poor nutrition and diet can lead to health problems, including obesity, diabetes, and hypertension. It is therefore important to make conscious decisions around both what we eat and when we eat.
It may help to plan ahead and have healthy food and snacks to hand and not shop when you are tired or hungry. Choose foods that are high in protein and low in saturated and trans fats (though it is important to have small amounts of mono- and polyunsaturated fats in your diet). Eat at least five to seven portions (80 grams each) of a variety of fruit and vegetables every day.
Staying hydrated will also help you maintain energy levels and concentration throughout the day. Official advice on how much fluid you need each day varies from country to country, but is generally around two litres (with around a fifth of this coming from the food that we eat). In general, it is a good idea to at least drink a glass of water with each meal and between meals; before, during and after exercise or physical activity; and if you feel thirsty.
Regularly walk, exercise or play sport.
There are many benefits to regular exercise that go beyond the obvious physical impacts of improving our cardiovascular health and strengthening our bodies. Research shows that regular exercise is one of the best ways to respond to stress, reduce anxiety, increase self-esteem, and improve sleep. Exercise causes a release of endorphins and other neurotransmitters (chemical messengers), including dopamine, norepinephrine, and serotonin. These brain chemicals all play important roles in regulating mood and lowering stress levels.
Higher-intensity exercise, including running, aerobics, and sports, will provide the greatest physical health benefits. But even making moderate activity, such as brisk walking or riding a bike, part of your daily routine will have positive impacts, particularly if you combine it with reducing sedentary behaviour the rest of the time. Incorporating activities that strengthen your major muscles, such as yoga or heavy gardening, is also important. Overall, it will help to choose activities that you enjoy and look forward to, rather than imposing a strict regime on yourself that you feel you should engage in but may frequently fail to do so. If you have a disability or decreased mobility, there will likely still be aerobic activities and resistance and flexibility exercises that will suit your physical abilities.
Incorporating regular exercise and physical activities into your schedule will also encourage you to take breaks and maintain a healthier work-life balance. For some people, team sports and other more social physical activities may offer additional benefits, as membership of a group offers us shared goals, social contact and a sense of connection, which all help improve wellbeing.
Address physical illness or injury, and give yourself time to heal.
It is tempting to believe that our work is so important and our workload so heavy that we do not have time to be sick. In fact, continuing to work when we are unwell is detrimental to both our short-term recovery and our long-term wellbeing. If you regularly ignore illness and injury, you may be contributing to the development of more serious and chronic conditions. You may also be drawn to relying on unhealthy coping mechanisms, such as excessive use of painkillers or drinking too much caffeine. In short, if you are wondering whether you are well enough to be productive, it is probably a good idea to stop, rest and recover.
Working through illness can also be detrimental to others. Infectious diseases can spread easily around a community or workplace and to beneficiaries and others that we work with. We may also affect our co-workers’ effectiveness and wellbeing if we are present, but irritable, distracted and unproductive.
It is important to explore whether recurring physical symptoms are linked to psychological pressures. Physical conditions, such as migraines and irritable bowel syndrome, may be at least partially triggered by stress and anxiety. Whatever the reasons behind your illness or injury, take the self-care approach and give yourself time to heal. Follow the guidance here on sleep, diet, exercise, meditation, avoiding drugs and alcohol, and staying in contact with close friends and family. Speak to a healthcare provider as soon as possible if you have any concerns.
Engage daily in self-reflection and contemplative practices.
We all have multiple and complex roles within our families, communities and workplaces. For many, the digital age means that we are contactable by co-workers and others whenever and wherever. And social media and the 24/7 news cycle demand our constant attention. Against this backdrop, it is important to make space for being over doing.
A wide range of everyday activities can aid self-reflection and contemplation. These include journaling, reading, gardening, cooking, or listening to music. Such activities can enhance our sense of balance, gratitude and wellbeing. Beyond that, there are many inward-facing or spiritual practices that help calm our minds, regulate our bodies, and create a greater sense of ease and contentment.
Meditation is a practice of contemplation and focus on a particular object, thought, sound, visualisation, movement, or the breath. Mindfulness meditation, in particular, has grown in popularity in recent years in line with increasing evidence of its effectiveness. Mindfulness is a psychological state of awareness; it is being present in the moment, without judgment. It has proven beneficial impacts on stress, focus, and emotional reactivity. You may be able to access meditation classes in a variety of traditions locally or you can pursue a daily solo practice with the help of a book or an app, such as Calm or Headspace.
If you are a person of faith, it may already be a cornerstone of your life to engage in meditation and contemplative prayer, and will likely find a deep sense of meaning in these and other spiritual practices.
Self-reflection can also be fostered through movement. For example, yoga is an ancient practice that supports health and relaxation through postures or poses and working with the breath and meditation. Alongside the physical benefits, it can reduce stress, anxiety and depression and improve sleep. Other forms of physical activity, such as walking in nature, may be your way of promoting relaxation and a sense of calm.
Do not use drugs or alcohol as a way of coping with stress or trauma.
The use of recreational drugs presents complex issues for health and wellbeing. Individuals, communities and societies all differ on questions of legality, abstinence, and the concept of harm. But be mindful that if you are breaking the law in the country that you are living in, then you are placing your livelihood and potentially your family life in jeopardy.
As a psychoactive substance that is socially acceptable in many societies, alcohol presents particular challenges. The ‘hidden alcoholism’ of those who regularly drink at the end of a busy or stressful day may risk negatively impacting family members, friends, and co-workers, as it can result in mood swings, tiredness and/or more-frequent illnesses. If you drink regularly, you should aim to have two or three alcohol-free days a week, and only drink in moderation at other times. But it is useful for each of us to consistently and honestly assess our choices around alcohol and be mindful of sliding into dependency. The Alcohol Use Disorders Identification Test (AUDIT), devised by the World Health Organization (WHO), can help you self-assess your alcohol consumption and identify any implications for your health and wellbeing. It is available in over 40 languages.
In general, signs that you have an unhealthy relationship with a substance include regularly having hangovers or comedowns, using drugs or alcohol when alone or secretly, and prioritising your access to drugs or alcohol over other personal and professional responsibilities. If you recognise any of these behaviours, you may find it helpful to talk with a healthcare provider or mental health professional. Be mindful that alcohol and other recreational drugs can interact with each other and with prescribed medication to reduce either’s efficacy or create unexpected and potentially serious effects.
Maintain relationships with friends, family, co-workers and community members who can support you.
Support from trusted others is the most important factor in preventing and mitigating the harmful effects of stress and poor wellbeing. Unfortunately, our pursuit of professional and personal goals, a passionate focus on a social or environmental cause, or simply a heavy workload can lead too many of us to neglect our relationships. Worse, we may sometimes channel frustrations and disappointments unhelpfully towards the ‘safest’ people in our lives: friends, family and co-workers.
It is crucial to nurture your key relationships. Try and ensure that there is openness, trust and mutual respect between you. If there are conflicts or rifts in your family relationships, ask yourself if and how they can be resolved, being mindful of any need to protect yourself from harmful relationships. If you do not live near your close friends and family, prioritise maintaining regular communication with them and ensuring that they feel connected to your daily life and you to theirs’. Be mindful of making time for children and elderly members of your family and community as individuals as well as in group settings.
It may be helpful to regularly examine your work-life balance to check that your priorities have not drifted away from your relationships without you realising. Be pro-active and make a conscious effort to set aside time to call or socialise with friends and family. Remember that social media, text messages and video calls can help us stay in touch and feel connected, but be careful not to let digital communication replace face-to-face contact when possible.
Understand what stressors might trigger changes in your health and wellbeing and learn to recognize the signs and symptoms of stress in yourself.
Stress is not always negative; sometimes, some stress can be good. It may motivate us and can push us to engage and achieve. When stress helps us to challenge ourselves and to be active, it can be positive, keeping us in our ‘green zone’. When we have too much stress in our lives, we can feel overloaded and overwhelmed. We can start to feel exhausted – instead of energised – and move into our ‘amber zone’.
Signs and symptoms of stress fall into five categories: physical, emotional, psychological, behavioural, and spiritual. In the physical realm, you may become tense, get backache or experience stomach problems. In the emotional realm, you may become angry, tearful or fearful. Psychologically, you may begin to doubt your competency or imagine that you are being judged harshly by others. Behavioural manifestations of stress may include unwise spending, smoking, speeding or avoiding people. Signs of spiritual loss of wellbeing may include questioning your faith or belief system, withdrawing from spiritual practices or breaking your own ethical codes.
Changes in any of these realms can indicate that our health and wellbeing is deteriorating. When this is prolonged, without suitable adjustments, our ability to cope diminishes. This can lead to unpleasant and even frightening symptoms and contribute to a range of physical and mental health disorders. Ultimately it can leave us burnt out and ill, pushing us into the ‘red zone’.
Try and build up a picture of what you look like in the different zones and what stressors might put you in the amber or red zone. If you move into the amber zone, it is important to do something about it straight away – do not wait until you get into the red zone, where it is much more difficult to recover. With stress and other mental and physical health concerns, including depression and anxiety, for example, it is important to know the warning signs. Be mindful of any negative changes in your sleep, appetite, mood and functioning. Follow the self-care guidance above on sleep, diet, exercise, meditation, avoiding drugs and alcohol, and staying in contact with close friends and family. If you have any concerns, speak to a healthcare provider or mental health professional as soon as possible.
end
The Holistic Security Protocol for Human Rights Defenders (the Defender’s Protocol) helps us advance our physical safety, digital security, and wellbeing and resilience. By following the Protocol, we enhance our individual and collective security, and can reduce the burden of attacks, harassment, and censorship on us and our communities. The Defender's Protocol was created by Open Briefing.
Licensed under Creative Commons BY-NC 4.0 license.